À l'ère des applications cloud-natives, des déploiements multi-cloud et de l'automatisation pilotée par l'IA, les identités numériques ont explosé en nombre et en diversité. Chaque microservice, agent d'IA, serveur MCP, conteneur, fonction et script sans serveur - sans parler des serveurs et applications traditionnels - agit comme sa propre "identité" au sein de l'infrastructure d'une organisation.
Mais cette prolifération d'identités non humaines (NHI) représente un défi imminent pour les entreprises en matière de cybersécurité : Chacune de ces identités virtuelles a besoin de privilèges d'accès et d'informations d'identification, mais la gestion et la sécurisation de ces informations d'identification à grande échelle ont dépassé les capacités des outils existants. C'est dans ce contexte que Battery Ventures est heureux d'annoncer ses nouveaux investissements aux côtés d'YL Ventures dans Hush Security*, une société qui contribue à mettre au point une approche sans secret de la gestion des identités et des accès pour les charges de travail en nuage.
Le défi de l'identité dans les environnements natifs de l'informatique en nuage et pilotés par l'IA
Par "sans secret", j'entends une approche qui n'exige pas que les systèmes conservent en permanence les identités sensibles des machines, c'est-à-dire les informations d'identification. C'est important parce que les organisations modernes sont aux prises avec une dangereuse prolifération d'identités sans précédent à l'échelle mondiale. Alors que les entreprises adoptent les architectures microservices, les fonctions sans serveur et les pipelines d'apprentissage automatique, le nombre d'interactions entre machines monte en flèche. Selon le rapport 2025 Identity Security Landscape de CyberArk, il existe aujourd'hui 82 identités de machines pour chaque personne au sein des organisations. Pourtant, la plupart des entreprises ne sont pas préparées, laissant ces machines dangereusement privilégiées et non gouvernées.
Chaque nouvelle intégration SaaS, chaque déploiement Kubernetes et chaque compte de service d'IA introduit une nouvelle identité non humaine qui doit être authentifiée et autorisée. Les solutions traditionnelles de gestion des identités et des accès (IAM), conçues à l'origine pour les personnes se connectant à des applications, sont mal équipées pour gérer le volume et la vitesse des identités des machines. De même, les équipes d'ingénieurs de Logiciel se sont appuyées sur des coffres-forts et des outils de gestion des secrets (comme HashiCorp Vault, Cyberark Conjure ou des solutions de gestion des secrets dans le nuage) pour stocker les clés API, les certificats et les mots de passe. Mais le simple stockage des secrets ne suffit pas lorsque le volume des informations d'identification double plus vite que les équipes ne peuvent le gérer. Les informations d'identification non gérées peuvent se répandre dans le code, les fichiers de configuration et les pipelines CI/CD, créant ainsi un terrain fertile pour les failles de sécurité.
Les conséquences de cette lacune sont déjà visibles. Le vol et la fuite d'informations d'identification restent l'une des principales causes d'incidents de sécurité, et les normes de conformité commencent à refléter l'urgence de meilleurs contrôles de l'identité des machines (par exemple, la norme PCI-DSS 4.0 renforce explicitement les exigences en matière de gestion des identités et des secrets). En bref, les environnements actuels centrés sur le cloud et l'IA exigent une nouvelle approche de l'identité et de l'accès - une approche qui traite les machines et les applications comme des identités de premier ordre et les sécurise de manière proactive. Les outils actuels qui se contentent de rechercher des secrets codés en dur ou qui exigent une rotation manuelle des secrets ne peuvent pas s'adapter à la nature dynamique et éphémère de l'infrastructure moderne.
L'appel à l'action est clair, et plusieurs startups ont commencé à répondre à cet appel en fournissant une visibilité sur la façon dont ces identités sont utilisées dans les environnements en nuage et sur site. La visibilité seule n'est cependant qu'une première étape.
La plateforme d'accès sans secret de Hush Security :
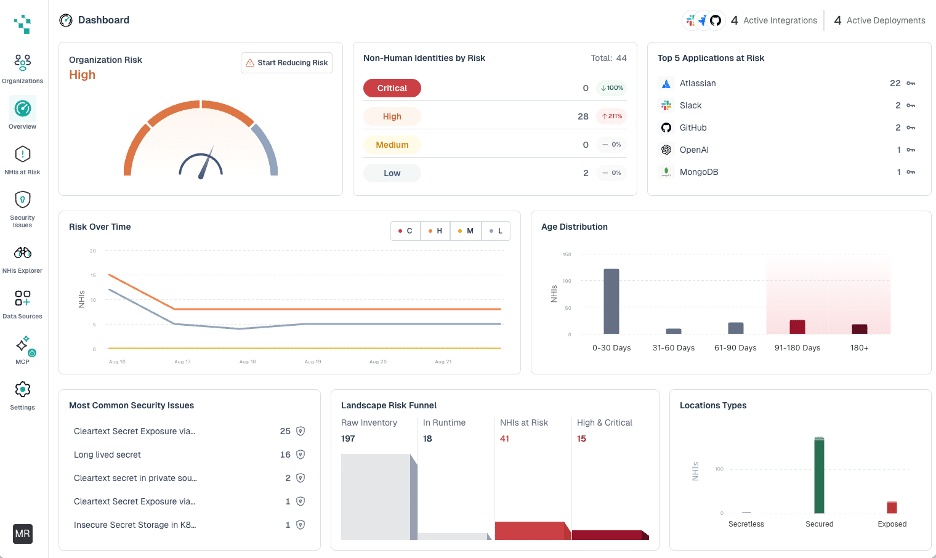
Hush Security propose une approche fondamentalement nouvelle : une plateforme qui rend les identités des machines invisibles. En termes plus simples, Hush permet aux applications et aux services de s'authentifier et de communiquer sans intégrer de secrets à long terme dans le code ou les fichiers de configuration. Il le fait par l'intermédiaire d'un agent et d'un déploiement sans agent. Le capteur de Hush fonctionne avec un minimum de surcharge tout en surveillant en temps réel les appels système et les requêtes réseau. Ce point d'observation permet de savoir en permanence où et quand les applications tentent d'accéder aux ressources. Lorsqu'une application doit se connecter à une base de données ou à une API, Hush peut injecter juste à temps un secret éphémère (credential) pour cette session, puis le révoquer, plutôt que de s'appuyer sur le fait qu'un développeur a stocké un mot de passe ou une clé quelque part à l'avance. Le résultat est puissant : Même si un attaquant intercepte un justificatif d'identité, celui-ci est éphémère et probablement inutile quelques instants plus tard.
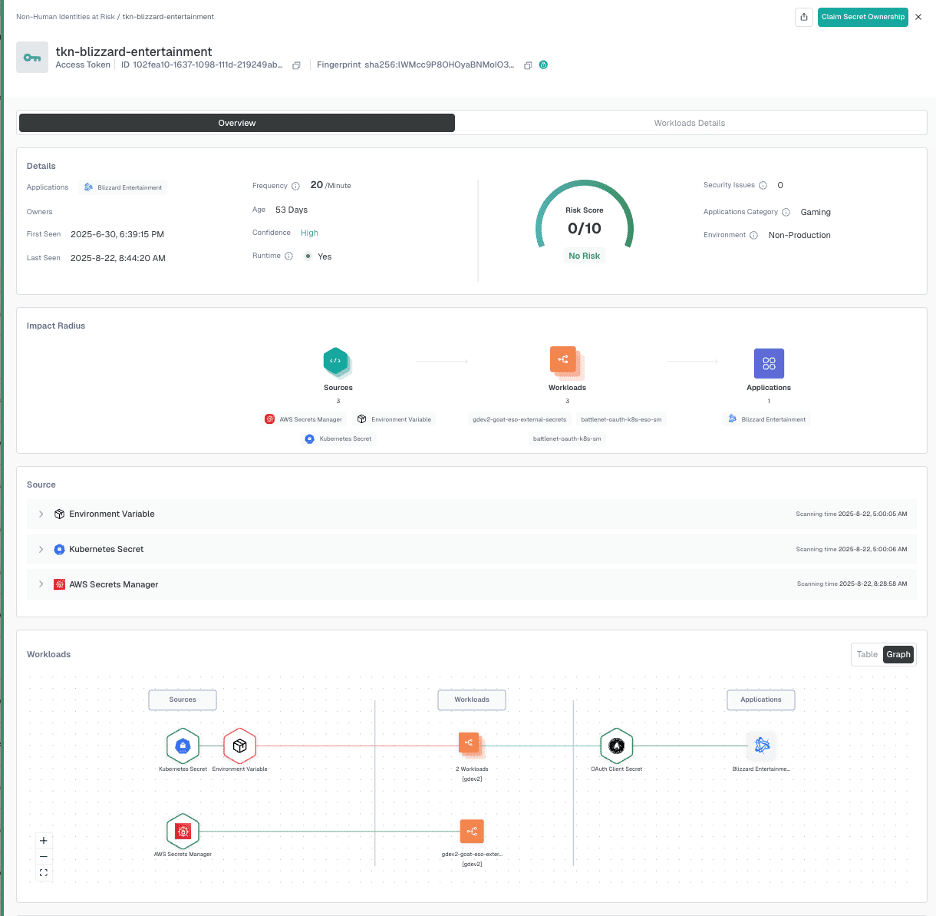
Cette approche d'injection de secret est associée à l'application et à l'inspection de politiques en temps réel. Le capteur de Hush ne se contente pas d'injecter des informations d'identification à la volée, il peut également vérifier en cours d'exécution que l'accès est légitime et conforme aux politiques de sécurité, ce qui revient à effectuer un contrôle d'accès adaptatif sur le moment. Les équipes de sécurité disposent ainsi d'un contrôle granulaire leur permettant d'autoriser ou de bloquer des actions en fonction du contexte (par exemple, bloquer une tentative d'accès inhabituelle même si les informations d'identification correctes ont été présentées). Il est important de noter que tout cela se passe en ligne, ce qui signifie que Hush ne se contente pas d'observer et d'alerter, mais qu'il est capable d'atténuer activement les effets, en bouclant la boucle de la détection à la réponse.
Peu de solutions offrent aujourd'hui ce niveau de visibilité et de contrôle intégrés au niveau de la charge de travail. Les coffres-forts traditionnels gardent les informations d'identification en sécurité au repos mais ne régissent pas leur utilisation, et les outils de contrôle purs peuvent signaler des anomalies après coup. En outre, les chambres fortes ne savent pas où les secrets sont utilisés, par qui, et si un grand nombre de secrets n'arrivent jamais dans les magasins secrets en raison de l'énorme retard accumulé par l'équipe d'ingénieurs. Ma propre expérience à la tête de grands groupes d'ingénieurs m'a permis de constater les coûts de coordination élevés de la gestion du cycle de vie des secrets et des certificats ("il est sur le point d'expirer !" / "il y a eu une fuite !" / "c'est le moment de l'audit !"). L'innovation de Hush consiste à combiner la visibilité, l'analyse et la correction au sein d'une plateforme unique, réduisant ainsi le risque de sécurité ainsi que la charge opérationnelle et le coût des chambres fortes secrètes existantes.
Soutenir une équipe conçue pour cette mission
Chez Battery, nous nous efforçons d'investir à la fois dans les grandes idées et dans les personnes capables de les mettre en œuvre. Dans Hush, nous voyons les deux. L'équipe fondatrice de Hush Security a une histoire remarquable de collaboration et de succès dans le monde des start-ups. Le PDG Micha Rave, le directeur technique Shmulik Ladkani, le vice-président de R&D Alon Horowitz et le CCO Chen Nisknorn ont tous travaillé ensemble auparavant en tant que cofondateurs ou dirigeants clés de Meta Networks, une startup israélienne de sécurité dans le cloud qui a été acquise par Proofpoint en 2019. Meta Networks a relevé le défi de l'accès au réseau sans confiance (ZTNA) en créant une plateforme de sécurité réseau native. Il s'agit donc d'une équipe qui connaît parfaitement les subtilités de la sécurité des entreprises. Leurs années d'expérience dans la conception de produits de réseau sécurisés (y compris l'intégration dans des environnements informatiques d'entreprise et l'expansion d'une activité de sécurité à l'échelle mondiale) nous rendent confiants quant à la voie à suivre pour cette nouvelle entreprise.
La passion de l'équipe pour résoudre le problème de l'identité des machines est palpable. Ils ont vécu les difficultés liées à la gestion des secrets et des identités de service dans leurs fonctions précédentes, et nous pensons qu'ils apportent le mélange parfait d'expertise et de pragmatisme pour s'attaquer à ce problème.
Avec Hush, nous voyons une entreprise qui trace une nouvelle voie pour l'authentification et la communication des machines, une voie qui pourrait redéfinir les meilleures pratiques en matière de sécurité dans les nuages. Nous ne pourrions être plus enthousiastes à l'idée de Partner avec cette équipe talentueuse pour faire de l'accès adaptatif et sans secret une réalité pour toutes les organisations tournées vers l'avenir. Tout comme la dernière décennie a vu une révolution dans la gestion de l'identité humaine (SSO, MFA, et confiance zéro pour les utilisateurs), nous pensons que la prochaine décennie verra une révolution dans la gestion de l'identité des machines, et Hush est prêt à être à l'avant-garde de ce mouvement.
Vous voulez que vos charges de travail ne soient pas secrètes ? Essayez-le : https://www.hush.security/
Les informations contenues dans ce commentaire de marché sont basées uniquement sur l'opinion de Barak Schoster Goihman, et rien ne doit être interprété comme un conseil d'Investissements. Ce matériel est fourni à titre d'information et ne constitue en aucun cas un conseil juridique, fiscal ou en matière d'investissement, ni une offre de vente ou une sollicitation d'une offre d'achat d'une participation dans un fonds ou un véhicule d'investissement géré par Battery Ventures ou toute autre entité Battery. Les opinions exprimées ici sont uniquement celles de l'auteur.
Les informations ci-dessus peuvent contenir des projections ou d'autres déclarations prospectives concernant des événements ou des attentes futurs. Les prévisions, opinions et autres informations présentées dans cette publication sont susceptibles d'être modifiées en permanence et sans préavis d'aucune sorte, et peuvent ne plus être valables après la date indiquée. Battery Ventures n'assume aucune obligation et ne s'engage pas à mettre à jour les déclarations prévisionnelles.
* Indique un Battery Portefeuille Investissements. Pour une liste complète de tous les investissements de Battery, cliquez ici.


Un bulletin d'information mensuel pour partager de nouvelles idées, des aperçus et des introductions pour aider les entrepreneurs à développer leurs entreprises.





